For those of you that were wondering, SQL Server isn’t the only platform which can be attacked via a SQL Injection attack. Apparently the MySQL.com website which hosts the official distribution channel for the MySQL database platform was attacked using good old SQL Injection earlier today (notice sent out via seclists.org including their schema).
Often I hear from MySQL professionals that MySQL isn’t susceptible to SQL Injection attacks. Apparently not only is it susceptible to SQL Injection attacks, but the company that writes the MySQL engine can’t correctly secure their website from being attacked. According to sucuri.net the “customer view application was used as the entry point, where the attackers were able to list the internal databases, tables and password dump…”. Not only was the password dump captured and posted only, but people have begun cracking the passwords, and some of these passwords are stupidly simple. The account sysadm (which I assume is pretty important) has a password of “qa”.
Apparently the Director or Product Management (who has 20+ years experience with most database platforms) used a 4 digit numeric password (probably his ATM pin code) as his password.
Needless to say, if you have an account on mysql.com and you use that password anywhere, you should probably change that password anywhere else that you use it.
If you think that your application is susceptible to SQL Injection attack, I recommend chapter 6 (SQL Injection Attacks) of “Securing SQL Server” which talks about how to prevent SQL Injection attacks. The examples which I provide are not SQL Server specific and the techniques shown to prevent SQL Injection attacks can be used against pretty much any relational database platform.
Denny
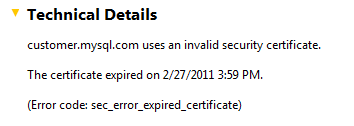
UPDATE (1pm PST 2011/03/27): Apparently the SSL certificate for logging into the MySQL.com website expired a month ago. The reason that I found this was that I was going to try and log in with my normal passwords (I’m pretty sure I have a mysql.com account) but with this error message, I’m not so sure about that. It’s probably OK, but still…
 Follow
Follow
“Often I hear from MySQL professionals that MySQL isn’t susceptible to SQL Injection attacks.”
What? Preventing SQL injection is part of just about any basic MySQL+PHP tutorial out there. Who are these people you’re finding?!
They’re certainly not “professionals”.
“Often I hear from MySQL professionals that MySQL isn’t susceptible to SQL Injection attacks.”
Who has ever said this? This line by itself makes me question the validity if this whole article.
I’ll find a site or two that I can site when I get back home. The I’m on the road at the moment. Give me a few hours.
@mrdenny: I don’t doubt that there are people saying “MySQL isn’t susceptible to SQL injection attacks,” of course there are. There are fools in every profession. But why would you ever have believed them? This SQL injection attack is embarrassing for MySQL, but you shouldn’t take it as evidence of those fools being wrong, you should have known they were obviously wrong the moment the words left their mouths. No references needed…
@mrdenny “Often I hear from MySQL professionals that MySQL isn’t susceptible to SQL Injection attacks.” – That is completely false. Maybe it isn’t susceptible to exactly the same attacks but there are attacks.
Ned,
Of course I knew they were wrong. However they are still giving out the bogus info about mysql. My post obviously (I hope) wasn’t a dig against MySQL but against people who don’t know how to correctly write software.
SQL injection is clearly a client issue. I understand that MySQL has a flag to make SQL injection much harder to do (I know a lot less about MySQL than I probably should) which is where I think a lot of newer MySQL users get the idea that SQL injection against MySQL isn’t possible.
Denny
I salute you, I really adore the way you treated the sub… maybe you could come to my site and tell some corrections. Thanks in advance
MySQL library provides a secure way of running sql queries. It’s named Prepared Statement.
It consist of question marks that you can pass to the method that execute the query. It’s very secure because you do not have to use quoting characters for the query parameters. That’s because they say MySQL is sql injection aware.
hey there and thanks for your information ? I have definitely picked up something new from proper here. I did alternatively expertise a few technical points using this site, since I skilled to reload the site lots of times previous to I may just get it to load correctly. I were wondering in case your hosting is OK? Not that I’m complaining, but sluggish loading circumstances times will often impact your placement in google and can harm your high-quality score if advertising and marketing with Adwords. Well I’m adding this RSS to my email and can look out for much extra of your respective intriguing content. Make sure you replace this once more very soon..
It is not my first time to go to see this website,
i am visiting this site dailly and take fastidious facts from here everyday.